OpenSea, the largest NFT marketplace by trading volume on the Ethereum blockchain, has issued a resolution to its current challenges that involves inactive listings.
This measure was done in response to a recent exploit on the platform in which several unidentified threat actors took advantage of OpenSea's upgrade process, and later scammed NFT users out of millions. The exact amount has not been identified, but Check Point Research, a threat intelligence research group that has been working on the the matter, estimates the damage to be over $3 million.
According to post-exploit analysis done by Check Point Research, threat actors exploited the upgrade process by making use of the same email from OpenSea and resending it to unaware users. Details on the previous OpenSea contract reveal that the atomicMatch request is sent to this address, and later transferred among other similar addresses with the Fake_Phishing initial. OpenSea uses the atomicMatch request parameter to provide minimal trust for trades on its NFT trading platform. An atomic transfer will only occur if all the conditions of a transaction are met.
Oded Vanunu, Head of Products Vulnerability Research at Check Point, shares some insight and advice on how to safely sign for NFT transactions:
"What should you do? Many websites and projects request a permanent access to your NFTs by sending you a transaction to sign. This transaction will give the websites/projects access anytime they want to your NFT unless you un-approve the transaction. Signing a transaction is similar to giving someone permission to access all your NFTs and cryptocurrencies. This is why signing is very dangerous. Pay extra attention to where and when you sign a transaction. Phishing emails may be tricky. We don’t recommend clicking on links from emails no matter who the sender is, always try to find the same information on the website provider."
Vanunu further explains the process behind the attack, listing the following steps which the exploit flows with:
- Victim clicks on a malicious link from the phishing email
- The link opens a phishing website and asks the victim to sign a transaction.
- By signing the transaction an atomicMatch_ request would be sent to 0xa2c0946ad444dccf990394c5cbe019a858a945bd (attacker contract).
- Attacker than forward the request to atomicMath at 0x7be8076f4ea4a4ad08075c2508e481d6c946d12b (OpenSea contract)
- OpenSea Contract verifies all the parameters of the deal and executes the transaction because everything is signed by the victim and approved.
- OpenSea contract communicate with the NFT contracts and transfer the NFT from the victim to the attacker according to the atomicMatch parameters.
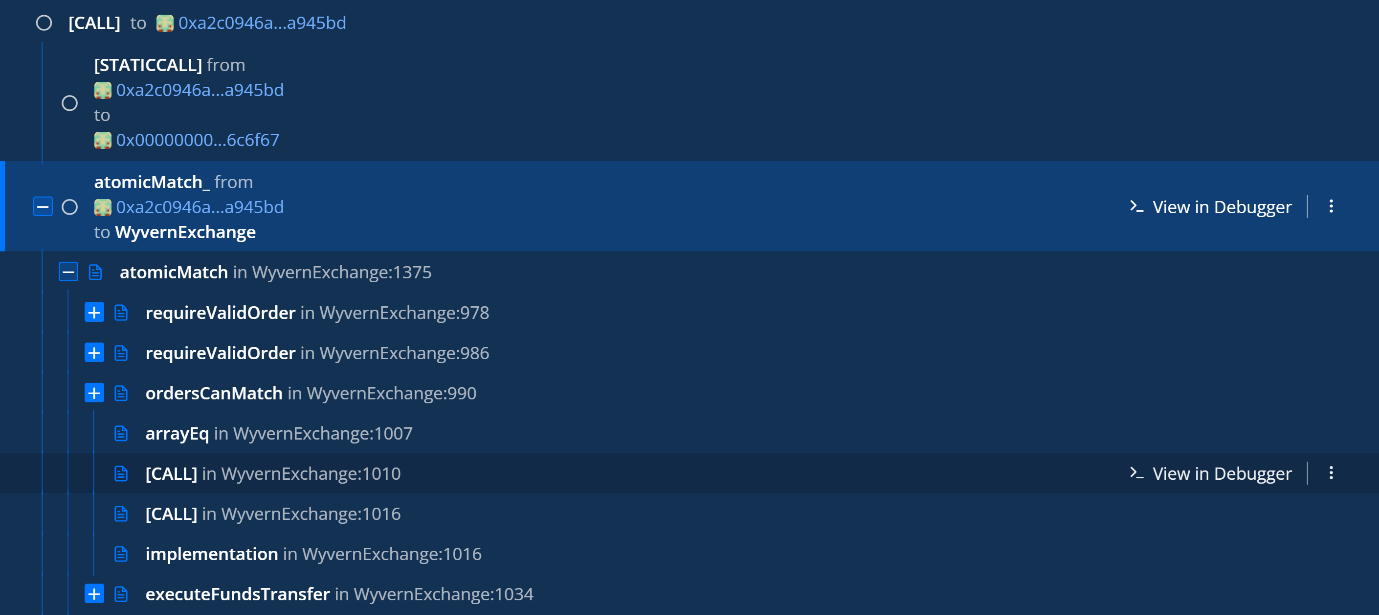
According to Check Point Research, the threat actor even goes on to execute a dry run to test and simulate the environment for the attack. The threat actor runs the same process and verifies the attack on OpenSea itself.
According to OpenSea, they are already implementing contract migration to curb and mitigate the extent of the exploit. This strategy is aimed at addressing the challenge of inactive listings for NFTs minted from an earlier time. With the contract migration, all OpenSea users who are about to or are already selling their NFTs on the platform will be required to transfer their listings, forwarded to a new smart contract on the Ethereum blockchain. OpenSea's has published a guide on how to do the migration safely.
Disclaimer: This article is provided for informational purposes only. It is not offered or intended to be used as legal, tax, investment, financial, or other advice.
Investment Disclaimer












