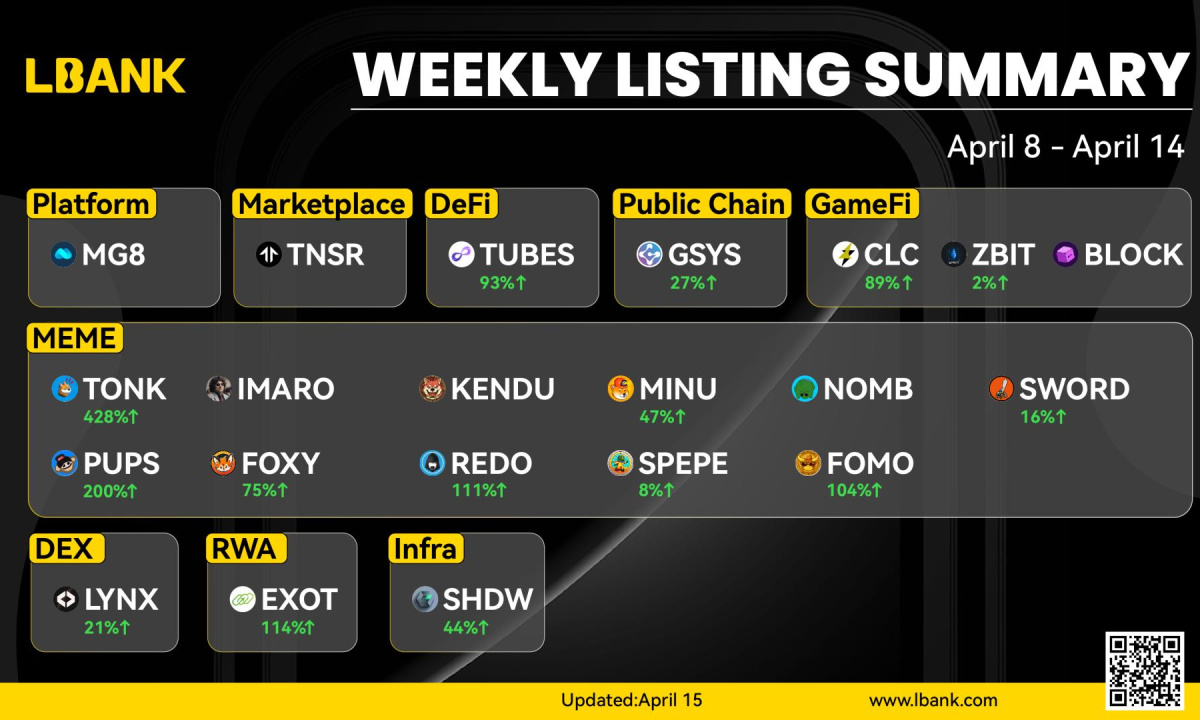
Table of Contents
- Cryptographic Hash Functions
- What is blockchain hashing?
- Mining
- Connecting blocks
- Creating keys
- Why is it important?
As soon as cryptocurrencies were invented and blockchain was established a lot of people found themselves dealing with terms and concepts that were unknown for a long time. It is still a very complicated field, which requires thorough knowledge and research.
One of the most prevalent concepts is hashing. Hashing is the creation of a sequence of characters (hashes) using a mathematical function. This sequence is characterized by a high level of security and allows you to send messages safely.
Most importantly it is part of every single cryptocurrency in the market right now, but all of them have different values and qualities so to say. One thing we can say for sure is that decent hashing is a part of every crypto’s success rate. When people voted one of the best regulated exchanges in the world a while back, most of the companies that made the top tier list all had a combined feature of listing only the most qualified currencies. These were mostly the big brands such as Binance and Coinbase, but others that dedicated resources to researching the coins they were listing also made the list.
Cryptographic Hash Functions
This is a specific type of hash that is secure and ideal for cryptography. Hash functions have the following features:
Determinism - at a particular input value, a fixed amount of hashes should be produced each time.
Computational efficiency - computer power should be sufficient to return hashes quickly. Most computers can process a hash function in a split second.
Resistance to finding an inverse image - A hash function should not give any information about giving out any information about the input value.
Collision resistance - Obtaining two inputs that could give two outputs. It must be very difficult or impossible. Since the length of the input value can be any, its variations are endless. The outputs have a fixed length and, accordingly, in this case, the number of options is limited. In this case, several inputs can produce the same output. If the resistance to collisions is not high enough, so-called Birthday attacks may occur. This is an attack in which mathematics prevails over probability theory. You may have heard of such cases. The simplest example of illustrating such attacks is that if there are 27 people in the room, there is a 50% chance that the two present have the same birthday.
Why is this happening? For one person, the probability is 1/365, based on the number of days in a year. The second person has the same probability. To determine the likelihood of coincidence of their birthdays, you need to multiply one indicator by another. So, it turns out that there are 365 dates of birthdays and 365 probabilities of coincidence, and if we extract the root from this number, it turns out that 23 randomly selected people have a 50% chance of matching birth dates.
If we apply this theory to hashing, it becomes clear that from a technical point of view, no hash function is fully collision-resistant, but it can take a very long time before this happens.
What is blockchain hashing?
Bitcoin operates on the basis of the blockchain and uses the SHA-256 hash algorithm (256 cryptographic hash algorithm). In the case of Bitcoin, hash functions perform three main tasks:
Mining
Miners compete for solving problems. Each miner takes information from the blocks that they already know about and build a new block from them. If the algorithm outputs a value smaller than the target digit, it is considered valid and can be accepted by other network participants. Thus, the miner gets the right to create the next block.
Connecting blocks
It is essential for added security. Each block in the blockchain is associated with the previous one, which is achieved through a hash pointer (variables that store the address of another variable). In fact, each block contains a hash result from the previous block in the blockchain. Thanks to this function, you can easily track the history in the blockchain and eliminate the likelihood of adding a malicious block to the network.
Creating keys
Private or public keys are required to send or receive cryptocurrency. Both keys are connected through a hash function. This is an integral component that excludes receiving receipt of your private key by third parties.
Why is it important?
The hash function provides cryptocurrency with a high level of security. And although in theory nothing is completely protected from hacking, this function provides the highest level of difficulty available today. We should understand that while cryptocurrencies are indeed anonymous and protected, in the modern world where everything depends on technology, no one is safe from cyber-attacks. Even the most protected system can be a subject of hacking. An intelligent and smart hacker could find a way to penetrate the system, but we should take all the measures to protect our network from any imminent attacks.
Investment Disclaimer